Getting Started with Sysmon for Linux.
If you’ve been paying close attention to social media late last week you may have seen a stream of posts relating to the release of Sysmon for Linux, marking the 25th anniversary of the Sysinternals toolset. In this post I’m going to take a brief look at Microsoft’s latest contribution to the Linux world.
Before we begin, installation steps are detailed here for SysinternalsEBPF (a requirement) and here for Sysmon for Linux.
Note that a large number of dependencies are required if building from source, but there are packages available for various distributions.
The precise installation steps aren’t detailed here as 1) these are likely to become redundant very quickly and 2) it’s always best to check the official repositories for the most up-to-date information.
Functionality
I’m going to take a brief look at the functionality provided by the Linux variant of Sysmon, but before that a configuration file will need to be supplied that details the events we’re interested in collecting.
By looking at the schema (sysmon -s) it’s possible to see what type of events can be captured – quite a large list… However, according to Microsoft’s blog, only a subset of these are currently supported by the Linux variant, which are detailed below.
| ID | Event Name | Filter |
|---|---|---|
| 1 | SYSMONEVENT_CREATE_PROCESS | ProcessCreate |
| 3 | SYSMONEVENT_NETWORK_CONNECT | NetworkConnect |
| 4 | SYSMONEVENT_SERVICE_STATE_CHANGE | – |
| 5 | SYSMONEVENT_PROCESS_TERMINATE | ProcessTerminate |
| 9 | SYSMONEVENT_RAWACCESS_READ | RawAccessRead |
| 11 | SYSMONEVENT_FILE_CREATE | FileCreate |
| 16 | SYSMONEVENT_SERVICE_CONFIGURATION_CHANGE | – |
| 23 | SYSMONEVENT_FILE_DELETE | FileDelete |
A minimal configuration (shown below) has been used to illustrate the format Sysmon will expect.
<Sysmon schemaversion="4.81">
<EventFiltering>
<ProcessCreate onmatch="include" />
<!-- Excludes ID 1 events (no inclusions defined) -->
<ProcessTerminate onmatch="include" />
<!-- Exludes ID 5 event (no inclusions defined) -->
<FileCreate onmatch="exclude" />
<!-- Includes all ID 11 events (no exclusions defined) -->
<FileDelete onmatch="exclude" />
<!-- Includes all ID 23 events (no exclusions defined) -->
</EventFiltering>
</Sysmon>The next step is to register (-i) or update (-c) the Sysmon configuration and view those logs.
After creating (ID 11) and deleting (ID 23) a test file, it’s possible to see these events are logged within the Syslog.
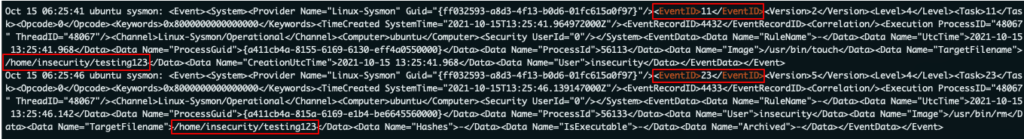
There’s plenty more to be tested here, Sysmon for Linux is obviously very new and it’ll be interesting to see if many real-world instances are configured in the near future.
In a future post we’ll likely detail how to push and parse this data to Azure Sentinel, but for now I hope this has been interesting reading.
About In.security.
In.security was formed by Will and Owen, two cyber security specialists driven to help other organisations stay safe and secure against cyber threats and attacks. After having worked together since 2011 in several former companies, they each gained considerable experience in system/network administration, digital forensics, penetration testing plus training. Based in Cambridgeshire, but operating nationally, we can provide a range of services and training for businesses and individuals alike. Read more about our services below:
- Penetration testing
- Vulnerability assessments
- Build reviews
- Red team testing
- Phishing assessments
- Password auditing
- Cloud security auditing