Hashcat P@ssw0rd Cracking: Brute Force, Mask & Hybrid.
In the first part we looked at basic hashcat usage and dictionary attacks. This time we’ll have a look at how to carry out brute force, mask and hybrid attacks.
Tl;dr, a brute force attack slowly increases the length, guessing every possibility, potentially forever. A mask attack is a subset of brute forcing, where we know elements of the password construction and as a result can reduce the number guesses to get it right. A hybrid attack combines a mask attack with a dictionary attack covered in the first part.
Brute Force
Brute forcing has limited applicability nowadays as it quickly becomes computationally infeasible to break passwords above certain lengths, generally 8, however this can vary depending on the algorithm and available resources. Attack mode 3 is brute force in hashcat and to brute force we need to tell hashcat to try every possible character (in the 95 printable ASCII character range). Shown below is how hashcat denotes the various character sets. For the purposes of this post we’re only going to cover the highlighted character sets.
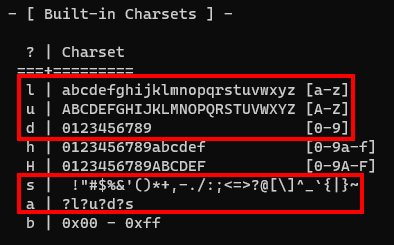
We can see that lower-alpha characters are denoted with l, upper-alpha with u, decimals with d and special characters with s. These four sets cumulatively comprise the 95 printable ASCII characters. There’s also ?l?u?d?s which is denoted by the letter a. You’ve probably joined the dots by now, a is a shortcut to call the aforementioned four character sets in one.
Now we know how to test for every character, we need to tell hashcat how long the password is. Clearly we’re not going to know this and after a certain length it’ll be nearly impossible to crack anyway, however let’s look at an example.
We tell hashcat the length of password we want to test by using ?a as noted above to represent each character. ?a?a would be a two character password, ?a?a?a?a a four character password and so on.
Let’s take the NTLM hash of the password *H4ck* and attack it in brute force mode.
hashcat -m1000 42EF98F2E9B77304716D2AECA2F0BD96 -a3 ?a?a?a?a?a?a?a
You may have noticed that our password is six characters long but we’ve added seven ?a‘s in hashcat. This won’t crack our hash because we’ve told hashcat to explicitly attack seven characters. To get around this we add ‐‐increment which tells hashcat to start at one character, then keep adding more until we’ve reached our target.
hashcat -m1000 42EF98F2E9B77304716D2AECA2F0BD96 -a3 ?a?a?a?a?a?a?a ‐‐increment
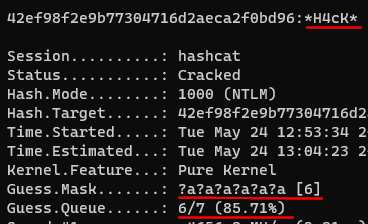
We see that hashcat kept guessing until it hit six characters and then found the password. Tl;dr, if you don’t know the password length, always use ‐‐increment. If you don’t know the length but don’t want to start at 1, you can assign a start point using for example ‐‐increment-min=5, where it would start from 5 characters and build up from there.
Mask Attacks
These have specific use cases where we know something about the password. For example:
- The password has 8 characters and we know the last one is a number
- The password can only be letters
- The passwords starts with P@ssw0rd and is followed by numbers
We often won’t know anything about the password of course, if for any reason we do, or when systems/applications impose character set constraints (generally due to poor development), mask attacks become more useful.
As mask attacks are a subset of brute forcing, they don’t have their own attack mode, they also use attack mode 3. Using the same character sets referenced in the brute force section, we can apply a mask and attack hashes. For example:
- Attacking a six-character lower-alpha password hashcat –a3 -m <$mode> <$hash/file> ?l?l?l?l?l?l
- Attacking the string P@ssw0rd followed by up to three numbers hashcat –a3 -m <$mode> <$hash/file> P@ssw0rd?d?d?d ‐‐increment
Custom Character Sets
Ok I get masks, but what if I don’t know if the last character could be either a number or special character?
Glad you asked. To save having to give hashcat a ?a and waste time guessing characters we know won’t be there, we can create a custom character set. Hashcat lets us create these using –1, -2, -3 and -4 switches. For example, if we know the last character of the password is either a decimal (?d) or special character (?s), we could set -1 ?d?s in hashcat, so when it sees ?1 in the mask, it’ll know to only test ?d and ?s values.
Here’s an example:
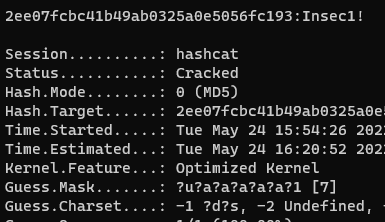
Attacking a seven character password that starts with a capital letter and the last character is either a number or special character would be:
hashcat -a3 -m0 2ee07fcbc41b49ab0325a0e5056fc193 -1 ?d?s ?u?a?a?a?a?a?1
Hybrid Attacks
Hybrid attacks combine a known/partially know element of a password, with a dictionary. We can either put the dictionary candidate first then add the mask, or vice versa, as shown by hashcat’s two hybrid attack modes 6 and 7.
This is one of the few times that hashcat has positional requirements. If using attack mode 6, the dictionary must come before the mask, similarly in attack mode 7 the mask must come before the dictionary.
For example:
hashcat -a 6 -m 0 <$hash> rockyou.txt ?d?d?d
hashcat -a 7 -m 0 <$hash> ?d?d?d rockyou.txt
Wrap Up
Although most tend to gravitate around dictionary based attacks, mask/hybrid attacks are very powerful and shouldn’t be overlooked. One common example is to use hybrid mode to add the year to the end of every dictionary guess, for example. Brute force attacks still have initial use in that you can exhaust every guess (the key space) of fast hashes up to (generally) eight characters and then focus on longer passwords.
Want to level up your password cracking further? We’re releasing our full Password Cracking 101+1 training FREE on our site over several weeks.
Stay tuned for some more password cracking tips and tricks.
Happy cracking!
About In.security.
In.security was formed by Will and Owen, two cyber security specialists driven to help other organisations stay safe and secure against cyber threats and attacks. After having worked together since 2011 in several former companies, they each gained considerable experience in system/network administration, digital forensics, penetration testing plus training. Based in Cambridgeshire, but operating nationally, we can provide a range of services and training for businesses and individuals alike. Read more about our services below:
- Penetration testing
- Vulnerability assessments
- Build reviews
- Red team testing
- Phishing assessments
- Password auditing
- Cloud security auditing