Hashcat P@ssw0rd Cracking: Attacking the Thought Process.
In part 1 we introduced some hashcat basics and in part 2 some other common attack styles were covered. Some of those are going to built on in this post as we look at building target specific wordlists and generating common/predictable patterns that we humans like to create. After all, passwords, like cyber security in general, is not a technical problem, but a people problem.
The Four Seasons of Passwords
The first group of people we’ll attack in this post are the seasonal password changers! This is a time old classic for password choices and regular password expiry results in predictable (seasonal) changes.
The password of Summer2022 is being used right now in an organisation near you! (You might find ! added at the end now and again)
This means we can also confidently say that many passwords will soon be changed to Autumn2022, and so on. This also conforms to Active Directory defaults that require any three of the available character sets. You could of course test a static season/year against your list, but as we can guess quickly, very quickly, we may as well widen our attack a bit. Let’s use a hybrid wordlist + mask attack.
Create a wordlist containing the seasons, which we’ll call seasons.txt. Then we need to consider our mask. We could just search for 2022, or we could search for 4 numbers where the first 2 are 20. Even though that would generate lots of years that haven’t happened yet, NTLM attack speeds will mean this exhausts quickly.
hashcat -a6 -m 1000 5F6B883D42910065A60FBDBFBFA27CAA seasons.txt 20?d?d
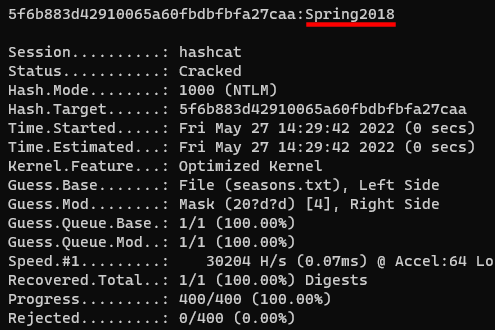
If you wanted to be more specific you could create a custom character set that only checks the numbers 0, 1 and 2 in the third position with the following, however, with such a small key space no performance gains will be observable.
hashcat -a6 -m 1000 5F6B883D42910065A60FBDBFBFA27CAA seasons.txt -1 012 20?1?d
Target Specific
So you’re doing an Active Directory password audit and have exhausted your dictionaries and rules. Where do you go next? Let’s get a bit creative.
Generate a wordlist of the words on your target organisation’s website. You’d be amazed how many times the name of an organisation’s services, software product, tech stack or even just an associated word, can find it’s way into someone’s password. A really popular choice is the company name and/or address, often with minor variations. If you’re assessing a large organisation called “Awesome Company”, I pretty much guarantee someone in there will have Aw3someC0mpany! or a similar variation as their password.
One way to create a targeted list is with cewl. An example command is shown below and the used switches highlighted in the help page.
cewl -d 2 -e -w wordlist_target.txt https://target.site -v
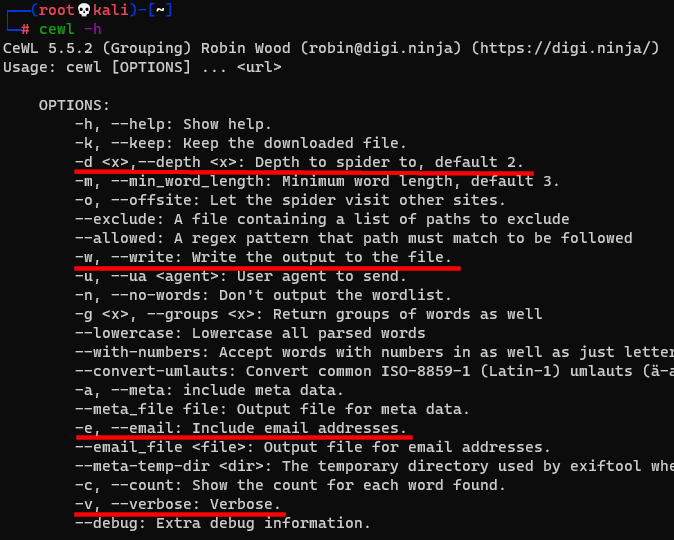
So the above command will look at the site https://target.site (starting at the root page), collect all the words it can and on any links it follows up to a depth of 2, e.g. https://target.site/products/amazing-product, will include email addresses and save the output to wordlist_target.txt. Doing a sort -u on that will result in a base wordlist that you can then give to hashcat with a big ruleset to generate lots of candidates, for example:
hashcat -m 1000 ad_hashes wordlist_target.txt -r rules\OneRuleToRuleThemAll.rule
Target Specific Hybrid Attacks
Your wordlist_target.txt generated earlier could also be used in a hybrid attack, for example:
hashcat -a6 -m 1000 <$hashlist> wordlist_target.txt ?a?a?a?a?a ‐‐increment
This will take every candidate from wordlist_target.txt and append up to five characters (all 95 printable ASCII characters) at the end, catching classic append patterns of numbers and/or special characters. There’s a hard limit on the number of ?a‘s you’ll be able to apply which ultimately comes down to hardware, but your available time, resources and attacked algorithm will definitely play a part.
Similarly, you can sometimes grab some low hanging fruit by applying a mask before the wordlist, for example, up to 4 numbers incrementing before the dictionary candidate:
hashcat -a7 -m 1000 <$hashlist> ?d?d?d?d wordlist_target.txt ‐‐increment
You could take this one step further and apply masks before and after your targeted word list. There’s no efficient way to do this in a single line, so we’ll split it into two parts: create a wordlist prepended with a mask, then use that wordlist and append a mask at the end.
hashcat -a7 -1 ?d?s ?1?1 wordlist_target.txt ‐‐increment ‐‐stdout > mask_list.txt
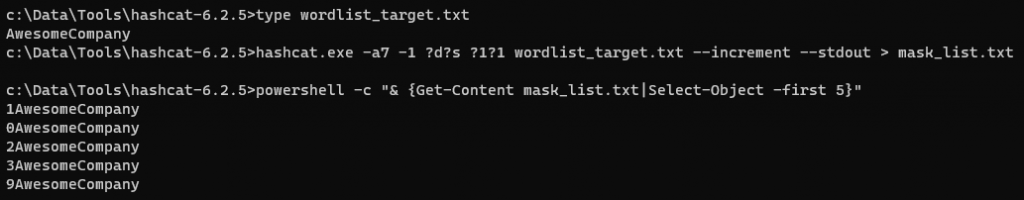
We created a custom character set (-1) that contains only numbers (?d) and special characters (?s) which could be a reasonable assumption for a characters that might be added at the start of a password. We then prepend every combination of one or two number/specials (?1?1 ‐‐increment) to every entry in wordlist_target.txt and write it to mask_list.txt, the truncated output of which can be seen above.
Now let’s take mask_list.txt as our dictionary and append a mask afterwards.
hashcat -a6 -m 1000 <$hashlist> mask_list.txt ?a?a?a?a?a ‐‐increment
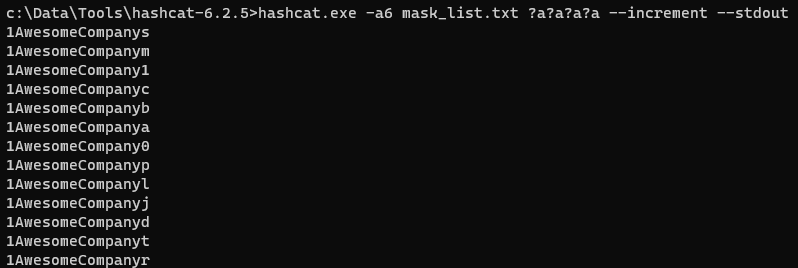
Now we’ll be testing passwords that start with up to 2 number/specials, followed by AwesomeCompany and then up to 5 of any character at the end.
Wrap Up
The methods covered here are just a few that could be used. Attack strategies will always be tailored to the target alongside hardware/time/algorithm considerations.
Hopefully, however, this has opened up a new way of thinking when it comes to attacking passwords, because although lots of us are doing passwords well, many of us still are not, so don’t overlook strategies like these that will often help attack the all too predictable password generation thought process.
That wraps up this short series of posts, but if you’re still hungry for more, check out our free Password Cracking 101+1 training.
Happy cracking!
About In.security.
In.security was formed by Will and Owen, two cyber security specialists driven to help other organisations stay safe and secure against cyber threats and attacks. After having worked together since 2011 in several former companies, they each gained considerable experience in system/network administration, digital forensics, penetration testing plus training. Based in Cambridgeshire, but operating nationally, we can provide a range of services and training for businesses and individuals alike. Read more about our services below:
- Penetration testing
- Vulnerability assessments
- Build reviews
- Red team testing
- Phishing assessments
- Password auditing
- Cloud security auditing