PsExec. I thought we were friends.
A couple of weeks ago we were talking a lot about monitoring and the wonderful world of Windows with a few delegates at BruCON. A valid point was raised regarding the monitoring of PsExec (and in general, service creation events) and false alarms.
We recently wrote a blog detailing certain detection metrics that could be used to link service installations and deletions, full details can be found here.
However, what if this common sysadmin tool is used commonly, for you know, common sysadmin purposes? After all which came first, the sysadmin or the APT…

A valid suggestion was raised by a delegate; perhaps sysadmins can use trusted service names for their activities and these could be filtered out at the SIEM. Before we go too far down this road; yes this could be abused by a malicious actor should they discover the naming convention used BUT there is a trade-off that we in security also have to acknowledge between usability and security. There will also no doubt be plenty of different methods and implementations that aid with mitigating false alarms, this is just one suggestion. Now with that disclaimer out of the way…
PsExec does have the functionality for you to assign a name to the service using the -r switch, shown below.
PsExec.exe \\$Computer -r TrustedAdmin cmd.exeLooking through both legitimate and illegitimate events, we can see our known legitimate event.
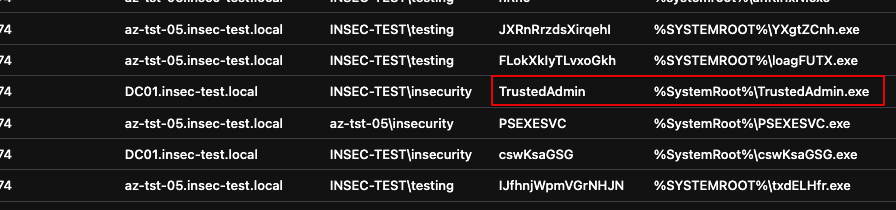
We can then use the KQL query (detailed here), but with the following addition to ensure all valid service creation events are firstly removed from the dataset (assuming the service has a trusted name of TrustedAdmin).
| where InstalledService != "TrustedAdmin"
Upcoming Events
If this has got your interest, we’re running our Defending Enterprises training at HITB in November.
About In.security.
In.security was formed by Will and Owen, two cyber security specialists driven to help other organisations stay safe and secure against cyber threats and attacks. After having worked together since 2011 in several former companies, they each gained considerable experience in system/network administration, digital forensics, penetration testing plus training. Based in Cambridgeshire, but operating nationally, we can provide a range of services and training for businesses and individuals alike. Read more about our services below:
- Penetration testing
- Vulnerability assessments
- Build reviews
- Red team testing
- Phishing assessments
- Password auditing
- Cloud security auditing