A cr4cking g00d time – walkthrough.
Warning: This post contains spoilers!
It’s been a few weeks since we released A cr4cking g00d time and we’d first like to thank everyone who gave it a go. We’ve received great feedback and are very pleased to hear that people have attained new levels of password cracking-fu in the process. Well done to @hops_ch who was the first to unlock the Ethereum wallet and claim the prize!
So without further ado, the walkthrough is detailed below.
Obtaining the challenge
The provided string base64 decoded into the URL where the file was located.
aHR0cHM6Ly9pbi5zZWN1cml0eS9kb3dubG9hZHMvQV9jcjRja2luZ19nMDBkX3RpbWUuemlw
which decoded to:
Note: This was formerly aHR0cHM6Ly9pbi5zZWN1cml0eS9kb3dubG9hZHMvQ3I0Y2tfTWVfSWZfWTB1X0Nhbi56aXA= which decoded to https://in.security/downloads/Cr4ck_Me_If_Y0u_Can.zip but this was updated in response to a conflicting challenge name which was an oversight on our part.
The password for the zip was the square root of the last four digits of our phone number to five decimal places. √1337 = 36.56501
Level 1
Hash: MD5
Method: rockyou wordlist
This was a raw MD5 hash which could be cracked with the rockyou wordlist:
./hashcat -m0 2cad29914ad447c4512a8390ec0a0d25 ../Dictionaries/rockyou.txt Password: thatwaseasy
Level 2
Hash: LM
Method: rockyou wordlist
Now we have an LM hash. Although some mistook this for an MD5 (both are 32 characters in length), you may have noticed that the second half of the hash was the ‘null’ LM value (highlighted in red below), indicating not only that we were dealing with an LM hash, but also that the password was 7 characters or less in length. Further details on LM hash construction can be found here.
./hashcat -m3000 E346B27838E0E932AAD3B435B51404EE ../Dictionaries/rockyou.txt
Password: OMG
Level 3
Hash: MySQL 4.1/5
Method: rockyou wordlist + rules (best64 or d3ad0ne)
A tool such as hash-identifier (comes installed with Kali) could have been used here to help narrow down your options to a MySQL hash or a raw SHA-1, both of which are 40 characters in length. We also now need to start mangling our wordlist with some rules. We tested using the above noted rules, however others may work too.
./hashcat -m300 5c53c6ff4bfaf0e8cd6d36781d1962a81497c073 ../Dictionaries/rockyou.txt -r rules/best64.rule
Password: !!secret!!!
Level 4
Hash: NTLM
Method: Mask attack
Now we get to break free from a wordlist and need to utilise mask attacks. This is a useful attack when a partial password is known and we want to try and brute force the remaining characters. The first part of the password was provided along with the character sets of the remaining characters, so we can use a mask that tells hashcat to try every possible combination of a given character set, in the position we specify.
hashcat –help shows us the masks for lowercase, uppercase, numbers and special characters are ?l ?u ?d and ?s, respectively.
./hashcat -m1000 -a3 CBFDDA957E87D1BDBB10C87AAF00AC4F ‘in.security?s?l?d?u?d?d?d?s’
Password: in.security%a1A272}
Level 5
Hash: Office 2013
Method: office2john followed by rockyou wordlist
Now we have a word document to play with. Some Googling will have revealed that we can use a tool called office2john (shipped with John the Ripper) to extract the hash from the file. Office docs have a complex hash which is significantly slower to attack so we chose a password that was fairly high up in the rockyou wordlist.
Step 1
./office2john.py Open_me.docx
Step 2
./hashcat -m9600 ‘$office$201310000025616cf6cfa7cc5fbf693d77d78e020c28d84dd7d596ccba83ff0260f6f50e4b82466*5969f62217c236e4a09bdb5b743b6aaeafb6e45ef54868deb97b021290220826’ ../Dictionaries/rockyou.txt
Password: mickeymouse
Level 6
Hash: MD5
Method: Mask + rockyou wordlist
Here we have a hash value to crack but the message states there were three unknown characters added at the start that might be numbers or special characters. This requires a hybrid attack comprmising of a mask + wordlist.
As we don’t know the positional requirements of the numbers / special characters we want to test each of the three places for both character sets. This can be done by assigning numbers and special characters to a custom mask. Hashcat allows us to create up to four custom masks using -1 -2 -3 and -4, followed by our chosen masks. We can then assign the custom mask to make sure we’re covering all bases.
./hashcat -m0 1202d6163f93919b4c4f476e7f61c06c -a7 -1 ‘?d?s’ ‘?1?1?1’ ../Dictionaries/rockyou.txt
Password: #0 Password Incorrect!
Level 7
Flag: Number of compliant policy masks
Method: policygen
The point of A cr4acking g00d time was not only to have some fun, but to help expand the knowledge of password cracking tools and their application. This challenge didn’t require any cracking, but to generate a list of masks that could be used to attack passwords given a specific password policy.
We hinted at a toolkit called PACK which contains policygen, a tool that does exactly what we want. Given a password policy where mixed alpha-numerics and special characters are used, and the minimum and maximum lengths are 8 and 12, respectively, we can run policygen as follows:
./policygen.py –minlength=8 –maxlength=12 –mindigit=1 –minlower=1 –minupper=1 –minspecial=1
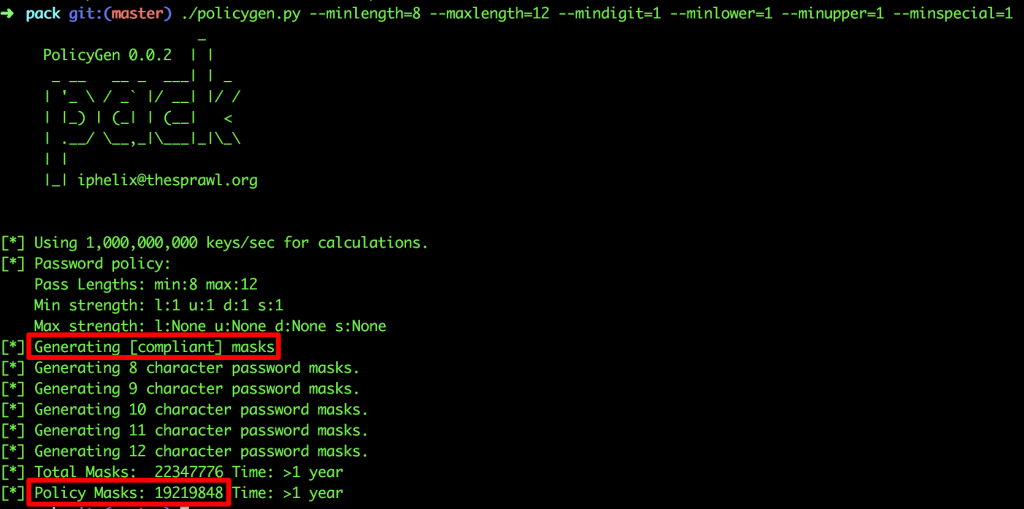
Flag = number of compliant policy masks (not the total number of masks) = 19219848
Level 8
Hash: MD5
Flag: The finding rule
Method: rockyou wordlist + best64 rule + debug mode + debug file
For this level cracking the password wasn’t enough. We wanted you to find the rule that was applied to the password candidate in order to derive the clear text value. We therefore needed to add some debugging options which are useful in providing statistical analysis about rule efficiency.
Running hashcat –help would show a number of debugging options, several of which would work for what we need, however the simplest is debug mode 1, which simply outputs the finding rule. Viewing the contents of your debug file reveals the flag.
./hashcat -m0 781660f9cc350c9e6ef7eb95387d255d ../Dictionaries/rockyou.txt -r rules/best64.rule –debug-mode=1 –debug-file=successful_rule
Flag: ] ] ] $1 $2 $3
Level 9
Hash: NTLM
Method: Combinator attack using 2x google-10000-english
Enter the combinator attack! This attack combines two wordlists and tries every combination of candidates from each. We also hinted at a great blog post from @netmux that details this attack and others very clearly.
./hashcat -a1 -m1000 5F54E0A905A3577C60F9C60290F40C46 ../Dictionaries/google-10000-english ../Dictionaries/google-10000-english
Password: encyclopediainfrastructure
Level 10
Hash: Winzip archive
Method: zip2john + rockyou wordlist
We threw you a slight curve ball here. The folder contained a file named SuperSecret.xlsx, however this was no Excel spreadsheet! This could be confirmed by viewing the file in a hex editor and researching the file signature as shown below. After identifying it was a Winzip file, we can use zip2john (shipped with John the Ripper) to grab the hash.
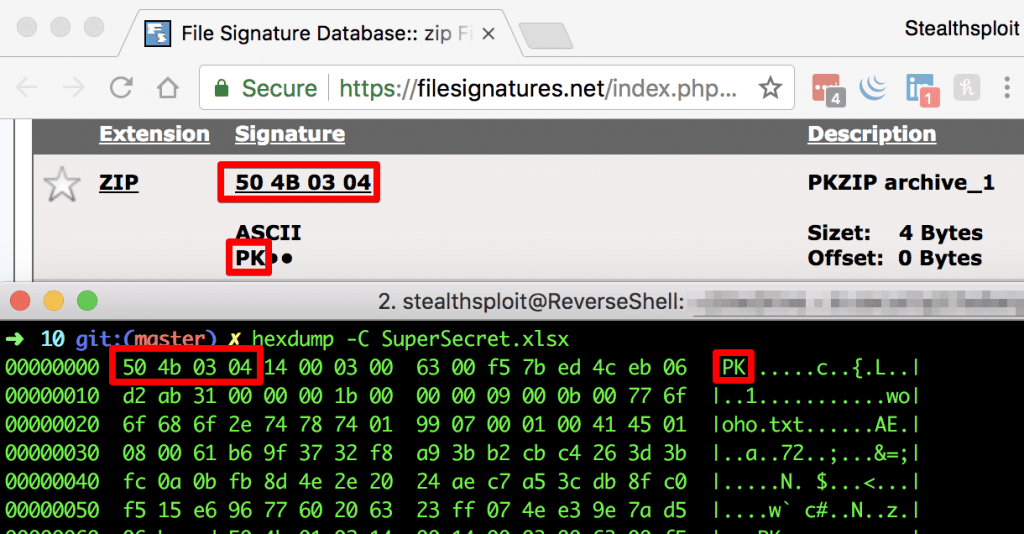
Step 1
./zip2john SuperSecret.xlsx
Step 2
./hashcat -m13600 ‘$zip2$01061b69f3732f8a93bb2cb1dc4263d3bfc0a0bfb8d4e2e2024aec7a53cdb8fc0f515e6967760206323ff074ee39e7ad506becd*$/zip2$’ ../Dictionaries/rockyou.txt
Password: tryharder!
Level 11
Hash: MD5
Method: Triple combinator attack
Here we hinted at the same blog post from level 9 and to crack it we need to expand our combinator attack further to include a third copy of the google-10000-english wordlist. To prepare, we need to create a single wordlist containing every possibility from two copies of the google-10000-english. We can then use this combined dictionary in a standard combinator attack, adding a basic google-10000-english as the second dictionary along side it. Let’s break it down…
Step 1
./combinator google-10000-english google-10000-english > google-10000-combined
Step 2
./hashcat -m0 -a1 839a98dcd1d0ac1d3faab54940008e6b ../Dictionaries/google-10000-english_combined ../Dictionaries/google-10000-english
Password: troubleshootingcardiovascularreconstruction
Level 12
Hash: MD5
Method: Brute force UTF-8 encoded hex attack
For the last challenge we hinted that the password is a 5-character Greek word (but the flag is the English translation) and provided a link to a UTF-8 encoding table. Googling would have resulted in good blogs on cracking foreign character passwords, which would also have given clues.
From the link in the hint we need to select Greek and Coptic from the dropdown to find the UTF-8 encoded Greek characters, each represented by two hex bytes. With knowledge of the hex, we can then tell hashcat to create two custom character sets (building on our knowledge of custom character sets from level 6).
The first custom character set needs to contain the every possible first hex byte of each Greek letter and the second custom character set needs to contain every possible second hex byte. In our case, the first custom character set is the first hex byte, which can only be either cd, ce, cf, d0 or d1. The second custom character set contains all the second hex byte options, which are shown in the long hashcat command below.
We also have to tell hashcat to assume the character set is given in hex, achieved with the –hex-charset switch. The final step is to provide a mask of 10 characters (even though we know the password is five Greek characters, each character requires two hex bytes).
./hashcat -m0 -a3 03e7200db4dfe1f85c9aff298e8fc2e7 –hex-charset -1 cdcecfd0d1 -2 b0b1b2b3b4b5b6b7b8b9babbbcbdbebf808182838485868788898a8b8c8d8e8f909192939495969798999a9b9c9d9e9fa0a1a2a3a4a5a6a7a8a9aaabacadaeaf ‘?1?2?1?2?1?2?1?2?1?2’
Password: Κρασί –> Wine
The Final Password
Concatenating all the passwords together provided the final password that unlocked the Ethereum wallet:
thatwaseasyOMG!!secret!!!in.security%a1A272}mickeymouse#0 Password Incorrect!19219848] ] ] $1 $2 $3encyclopediainfrastructuretryharder!troubleshootingcardiovascularreconstructionWine
About In.security.
In.security was formed by Will and Owen, two cyber security specialists driven to help other organisations stay safe and secure against cyber threats and attacks. After having worked together since 2011 in several former companies, they each gained considerable experience in system/network administration, digital forensics, penetration testing plus training. Based in Cambridgeshire, but operating nationally, we can provide a range of services and training for businesses and individuals alike. Read more about our services below:
- Penetration testing
- Vulnerability assessments
- Build reviews
- Red team testing
- Phishing assessments
- Password auditing
- Cloud security auditing