Using Kibana and Packetbeat to map DNS queries.
Overview
In this short post we’re going to show one visual method of mapping, and potentially identifying malicious DNS traffic within a network. We’re not going to walk through the configuration of Elastic, beats agents or Kibana and there is an assumption that UDP 53 traffic is being logged by Packetbeat on the endpoint(s).
Visualisations
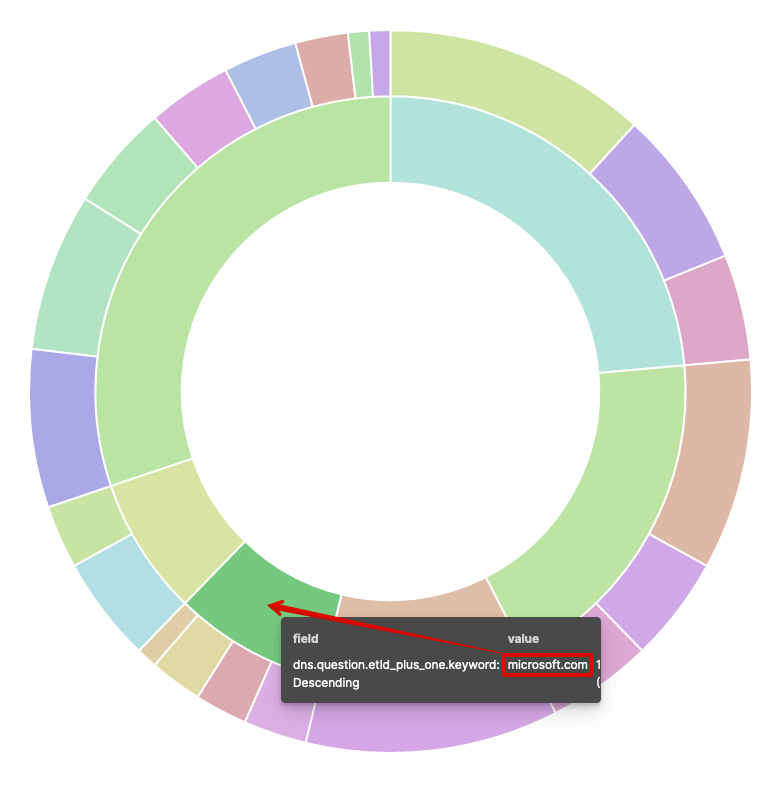
The below visualisation will be the end product of this exercise. This is a pie chart with two slices per segment. The inner slice denotes a TLD (in Kibana speak, this is mapped to dns.question.etld_plus_one.keyword), i.e. microsoft.com, as shown in the below image.
The outer segments denote queries to that particular domain (in Kibana speak, this is mapped to dns.question.name.keyword), i.e. in this example, watson.telemetry.microsoft.com, as shown in the image below.
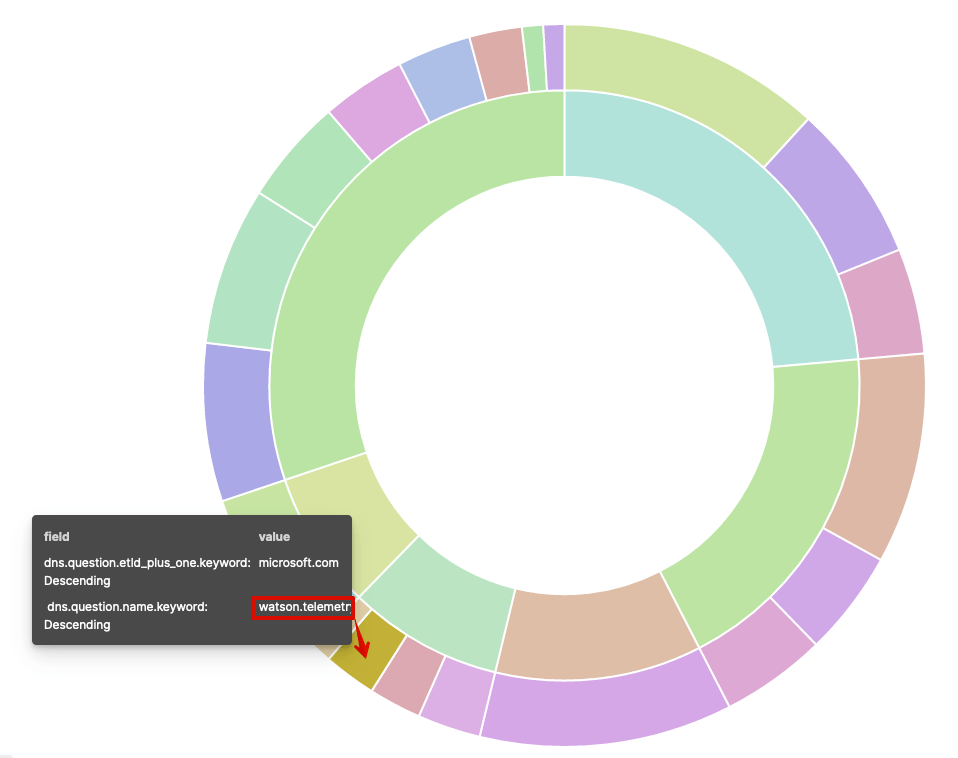
What’s interesting here is if someone is performing a lot of different queries to a particular domain (and we mean A LOT of queries) then this visualisation quickly makes it apparent that something strange is going on.
Take a look at the following video. We have mimicked this attack in our lab using the dnscat2 server from iagox86 (https://github.com/iagox86/dnscat2) running on the attacking host and the PowerShell dnscat2 client from Luke Baggett (https://github.com/lukebaggett/dnscat2-powershell) has been executed on the target, but the same behaviours using other tools based on the same methods would be just as revealing.
The suspicious domain quickly becomes evident (pwned.network) and seeing this graphic on the wall of your SOC would no doubt raise a few eyebrows!
If you want to recreate this, here’s our Kibana visualisation configurations.
Visualisation
- Type: Pie
- Source: Packetbeat
Metrics
- Slice size: Aggregation / Count
Buckets
Split slices (inner)
- Aggregation: Terms
- Field: dns.question.etld_plus_one.keyword
- Order by: Metric / Count
- Order: Descending / Size 5
- Group other values in a separate bucket: Selected
Split slices (outer)
- Sub aggregation: Terms
- Field: dns.question.name.keyword
- Order by: Metric / Count
- Order: Descending / Size 150
About In.security.
In.security was formed by Will and Owen, two cyber security specialists driven to help other organisations stay safe and secure against cyber threats and attacks. After having worked together since 2011 in several former companies, they each gained considerable experience in system/network administration, digital forensics, penetration testing plus training. Based in Cambridgeshire, but operating nationally, we can provide a range of services and training for businesses and individuals alike. Read more about our services below:
- Penetration testing
- Vulnerability assessments
- Build reviews
- Red team testing
- Phishing assessments
- Password auditing
- Cloud security auditing